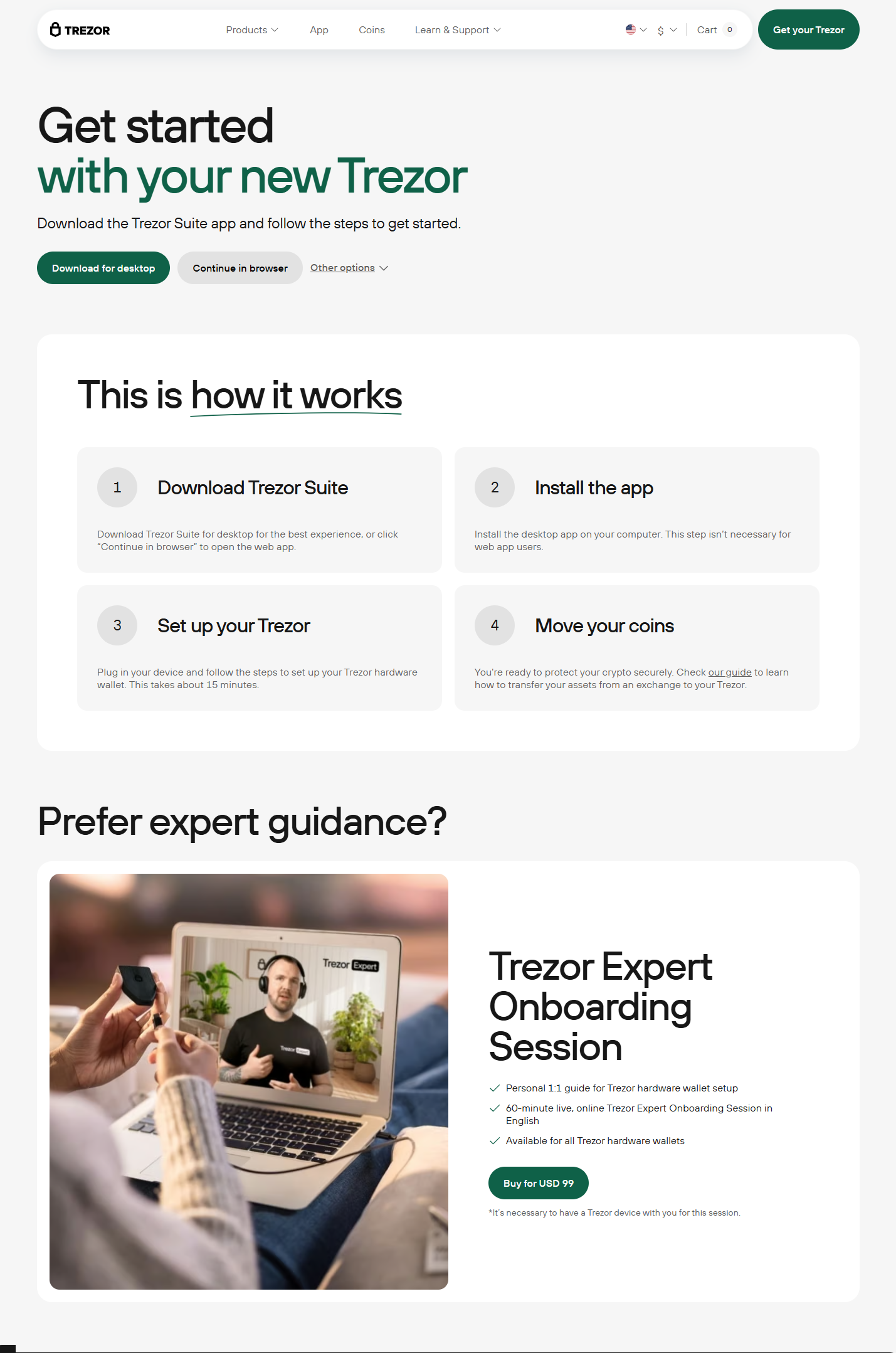
Trezor Bridge v25.2.2 – A Secure Gateway for Crypto Management
Introduction
Trezor Bridge v25.2.2 is the latest version of Trezor’s secure communication software that connects your Trezor hardware wallet with supported browsers and applications. This update enhances security, stability, and performance, ensuring seamless interaction between your device and Trezor Suite. Whether you're managing cryptocurrencies or executing transactions, Trezor Bridge provides a smooth, efficient, and secure experience.
Key Features of Trezor Bridge v25.2.2
- Enhanced Security: Improved encryption methods to safeguard sensitive data.
- Faster Performance: Optimized processing speeds for quick wallet interactions.
- Broader Compatibility: Seamlessly works with major browsers and OS platforms.
- Improved Connectivity: Ensures a stable connection between your Trezor wallet and browser.
- Bug Fixes & Updates: Addresses previous issues to enhance user experience.
Step-by-Step Guide to Install Trezor Bridge v25.2.2
Step 1: Download the Latest Version
- Visit the official Trezor website.
- Navigate to the Downloads section and select Trezor Bridge v25.2.2.
- Choose the correct version for your operating system (Windows, macOS, or Linux).
Step 2: Install Trezor Bridge
- Open the downloaded file and follow the installation prompts.
- Grant necessary permissions for the software to run on your device.
- Once installed, restart your browser for changes to take effect.
Step 3: Connect Your Trezor Wallet
- Plug your Trezor hardware wallet into your computer.
- Open Trezor Suite and wait for the device to be recognized.
- Follow on-screen instructions to complete the setup.
Step 4: Verify Connection
- Check if your Trezor wallet is detected within the Trezor Suite.
- If prompted, update firmware and security settings.
- Once verified, you’re ready to securely manage your cryptocurrencies.
Advanced Benefits of Trezor Bridge v25.2.2
1. Unparalleled Security
Trezor Bridge ensures a direct and encrypted connection between your wallet and Trezor Suite, preventing unauthorized access and phishing attempts.
2. Seamless User Experience
The latest version offers an intuitive interface and automated updates, reducing manual configurations and improving overall ease of use.
3. Cross-Platform Compatibility
Supports Windows, macOS, and Linux, ensuring a smooth experience across multiple operating systems without requiring additional configurations.
4. Optimized Performance
With improved processing capabilities, transactions and wallet interactions are significantly faster, enhancing the efficiency of crypto management.
5. Regular Updates & Fixes
Trezor continuously updates the Bridge software to fix vulnerabilities and enhance features, keeping your device safe from evolving threats.
FAQs
1. What is Trezor Bridge used for?
Trezor Bridge acts as a communication layer between your Trezor hardware wallet and web applications, enabling secure transactions and wallet management.
2. Is Trezor Bridge v25.2.2 safe to use?
Yes, Trezor Bridge v25.2.2 features enhanced encryption and security protocols to protect user data and transactions.
3. Do I need Trezor Bridge for Trezor Suite?
Yes, Trezor Bridge is necessary for enabling a secure connection between your Trezor wallet and Trezor Suite on supported browsers.
4. How do I update to Trezor Bridge v25.2.2?
Simply download and install the latest version from the official Trezor website, replacing any older versions automatically.
5. What should I do if my Trezor wallet is not detected?
- Ensure Trezor Bridge is installed correctly.
- Restart your browser and reconnect your device.
- Check USB cables and ports for proper connection.
- Visit Trezor support if issues persist.
Final Thoughts
Trezor Bridge v25.2.2 is a vital upgrade for users seeking secure and seamless crypto management. With enhanced security, improved speed, and better compatibility, this version ensures an optimal experience for Trezor wallet users. By following the installation and setup guide, you can confidently manage your digital assets while staying protected from online threats.